Why FFT Perimeter Intrusion Solutions Are Essential for Effective Surveillance
Why FFT Perimeter Intrusion Solutions Are Essential for Effective Surveillance
Blog Article
Comprehending the Relevance of Information and Network Security in Today's Digital Age
In an era where digital transformation is indispensable to business success, the significance of information and network protection has never been more obvious. As companies increasingly incorporate sophisticated innovations, they additionally expose themselves to a myriad of cyber threats that can endanger delicate info and disrupt procedures. Comprehending the effects of data breaches, together with the necessary protection procedures needed to reduce these risks, comes to be vital. The obstacle lies not only in implementing these actions however also in growing a positive security culture within organizations. This conversation will explore these complexities even more and reveal important insights on guarding digital assets.
The Rise of Cyber Hazards
The landscape of electronic safety and security has ended up being progressively risky as cyber hazards multiply around the world. Organizations across different markets are encountering a rise in innovative attacks, ranging from ransomware to phishing schemes. These hazards not only jeopardize sensitive data however additionally interfere with business operations, bring about significant economic losses and reputational damages.
Furthermore, the introduction of innovative techniques such as fabricated intelligence and device understanding has actually geared up opponents with the devices to automate their operations, making it significantly testing for traditional safety and security measures to keep up. As services navigate this treacherous landscape, the urgency for durable data and network protection methods has never been greater, highlighting the requirement for watchful surveillance, prompt updates, and staff member recognition to mitigate these rising hazards.
Consequences of Information Violations
Data violations can have extreme and significant implications for organizations, impacting not only their economic standing but also their credibility and client trust fund. When sensitive details is compromised, companies often deal with direct economic losses as a result of legal charges, governing fines, and the expenses related to occurrence reaction. Furthermore, the lasting impacts can be even a lot more damaging; a ruined reputation may cause shed service possibilities and declining customer retention.
The disintegration of customer count on is possibly one of the most dangerous repercussion of a data violation. Customers may wonder about an organization's ability to secure their individual information and, because of this, may pick to take their service in other places. This loss of confidence can result in lowered profits and market share.
Furthermore, companies might experience enhanced examination from regulators and stakeholders, causing an extra difficult functional environment. The emotional effect on staff members, that may really feel much less safe or valued, can also affect performance and spirits.

Important Safety And Security Measures
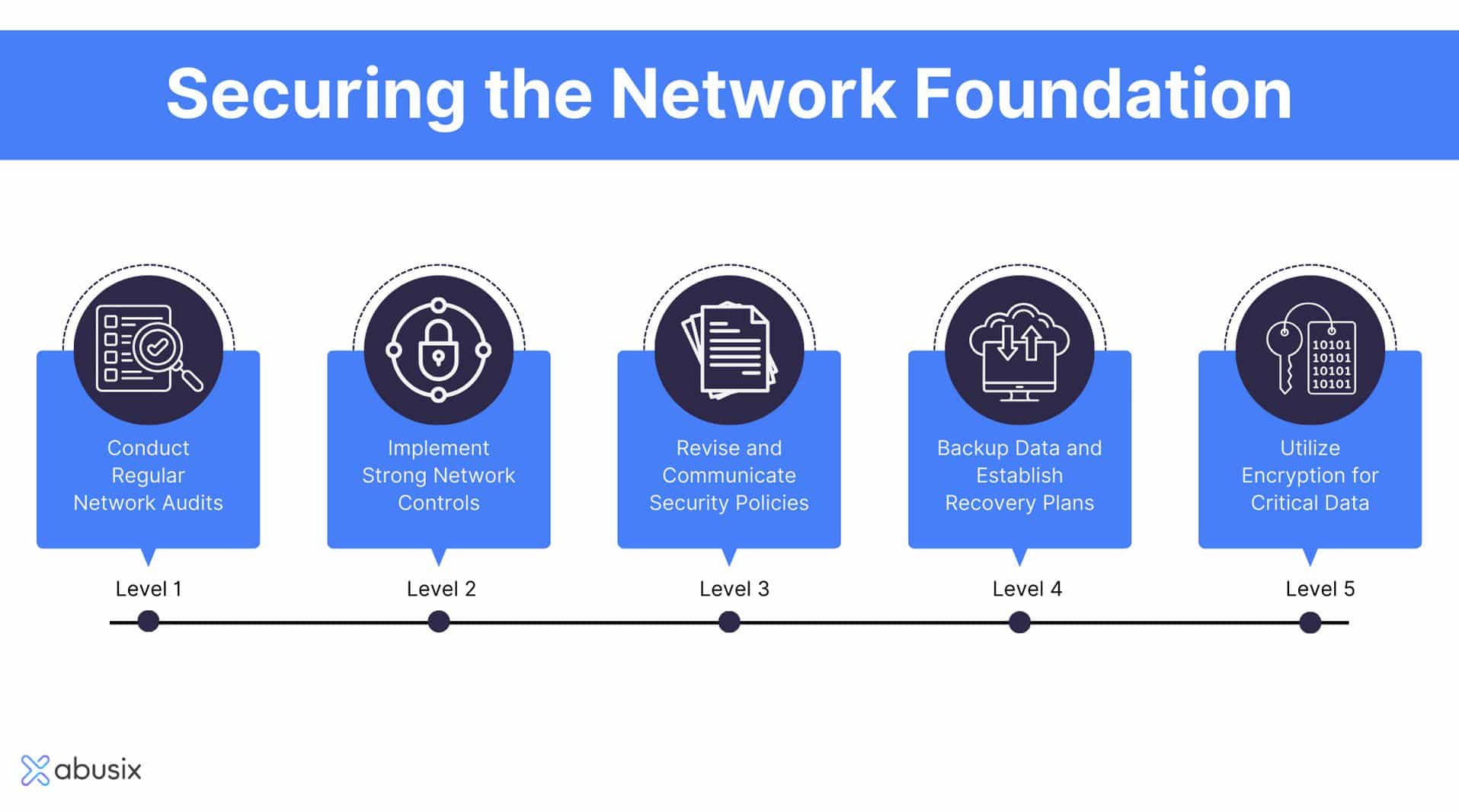
Executing important protection measures is critical for safeguarding sensitive details and maintaining business honesty. Organizations must adopt a multi-layered security technique that encompasses both electronic and physical safeguards.
Among the foundational steps is to establish robust accessibility controls, ensuring that only authorized personnel can access delicate information. This can be accomplished through solid password plans, multi-factor authentication, and regular audits of customer accessibility civil liberties. Additionally, encrypting data both en route and at rest provides a necessary layer of defense against unauthorized accessibility.
Routine software application updates and spot administration are also essential, as they help alleviate vulnerabilities that could be manipulated by destructive stars. Organizations ought to carry out firewalls and intrusion detection systems to monitor network web traffic and determine prospective hazards proactively.
In addition, carrying out routine safety analyses and infiltration testing enables organizations to determine weaknesses in their defenses before they can be he has a good point manipulated. Employee training on safety and security understanding is similarly crucial, as human mistake continues to be among the leading sources of information breaches. By integrating these necessary protection procedures, companies can dramatically decrease their risk exposure and boost their strength versus cyber hazards.
Structure a Safety And Security Culture
Developing an effective protection society within an organization is an important complement to carrying out robust safety measures. A safety and security society cultivates a setting where workers understand the importance of safeguarding sensitive details and are actively taken part in guarding it. This society is cultivated via detailed training programs that emphasize the importance of data security and the possible risks connected with negligence.
Management plays a critical function in developing this culture. Employees are more most likely to adopt comparable attitudes when executives prioritize protection and demonstrate their dedication. Regular interaction concerning safety and security updates, policies, and treatments guarantees that every person remains attentive and informed
Motivating open discussion concerning protection concerns equips staff members to report dubious activities without concern of retribution. Carrying out a benefits system for aggressive behavior can even more incentivize people to take possession of safety and security techniques.
Additionally, conducting drills and simulations aids reinforce the value of readiness and feedback. By incorporating safety and security right into decision-making processes and daily operations, companies can develop a resilient workforce efficient in adapting to developing dangers. Inevitably, a solid security culture not only safeguards data however likewise improves total business stability and reliability.
Future Trends in Information Security
Emerging technologies and developing cyber dangers are reshaping the landscape of data security, prompting organizations to adapt their strategies as necessary. One substantial fad is the enhanced fostering of synthetic intelligence (AI) and artificial intelligence (ML) for risk detection and response. These modern technologies make it possible for more positive protection procedures by evaluating vast quantities of information to determine anomalies and possible violations in real-time.
One more trend is the action in the direction of zero-trust safety and security models, which run under the concept that no individual or device must be relied on by default. This approach highlights continuous confirmation visit site and reduces accessibility to delicate data based upon strict verification procedures.
In addition, the increase of remote job has increased the need for durable endpoint safety solutions that shield devices outside standard network perimeters - data and network security. As companies embrace cloud computer, safeguarding information in this content transportation and at rest has come to be critical, resulting in the advancement of advanced encryption techniques
Verdict
In verdict, the importance of information and network safety can not be overemphasized in the contemporary digital landscape. As cyber threats continue to intensify, companies need to stay cautious and aggressive in carrying out detailed protection actions.
In an age where digital change is indispensable to business success, the significance of information and network safety has never been more pronounced. Understanding the effects of data breaches, along with the crucial protection steps needed to minimize these dangers, becomes crucial.Developing an efficient safety and security culture within an organization is a crucial complement to implementing durable safety and security measures.Progressing and emerging modern technologies cyber dangers are reshaping the landscape of data security, motivating companies to adapt their methods as necessary.In verdict, the relevance of data and network safety can not be overstated in the contemporary digital landscape.
Report this page